Private Container Registries
Shipyard supports pulling images from private registries including AWS/ECR, Docker Hub, GCP/GCR, Quay, GitHub Packages, and JFrog Artifactory.
To access your Organization Settings page, click on Settings at the top of your main dashboard:
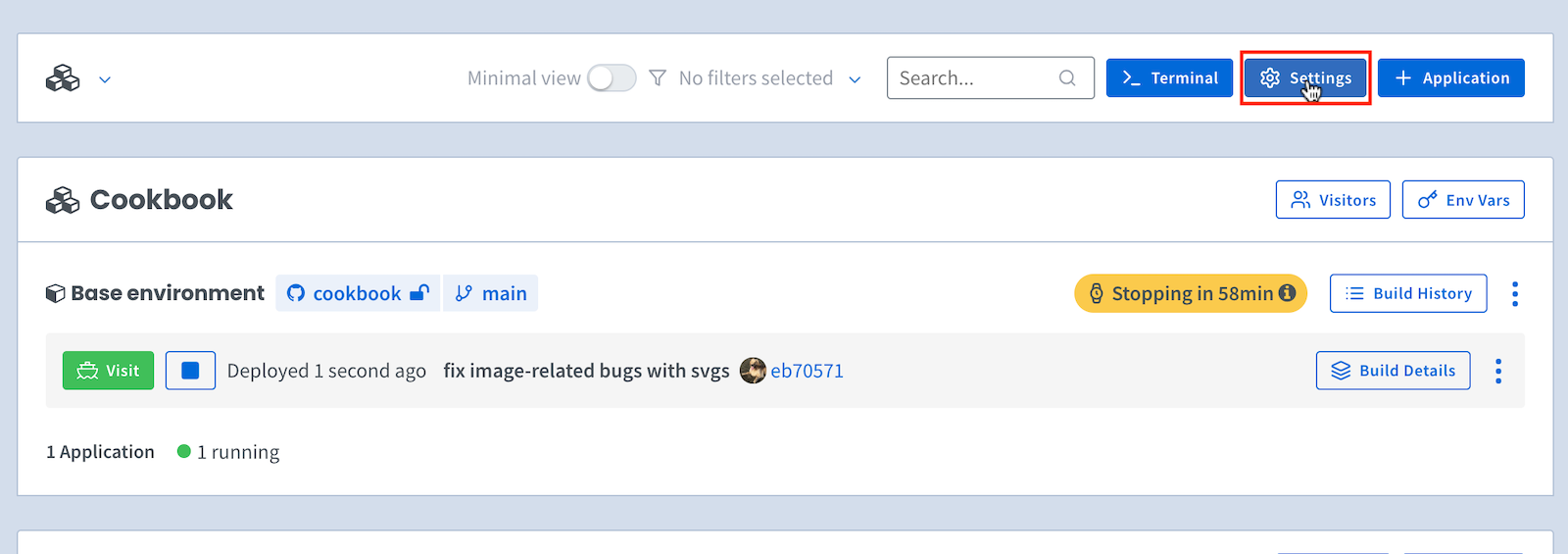
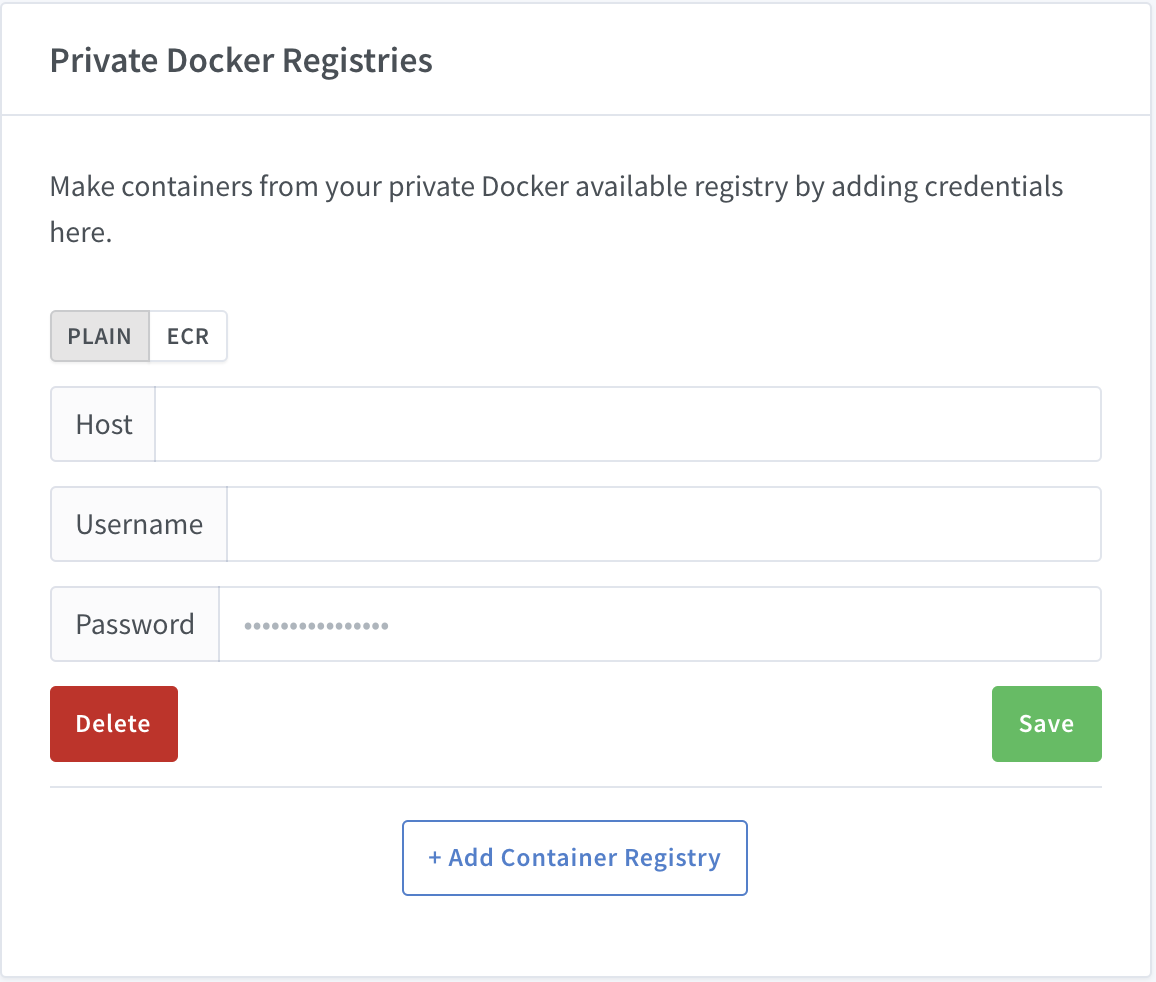
You can add credentials from the Private Docker Registries section on your Org Settings page.
- AWS/ECR
- Docker Hub
- Google Container Registries
- Quay
- GitHub Packages
- JFrog Artifactory
When adding registry credentials, select the ECR option.
- Host:
[your ECR host] - Access Key:
[your AWS access key] - Secret Key:
[your AWS secret key] - Region:
[the ECR region, like us-east-1]
The AWS user needs read access to ECR via IAM.
Here's a read-only policy straight from the AWS docs which would grant AWS ECR access to a Shipyard user:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ecr:GetAuthorizationToken",
"ecr:BatchCheckLayerAvailability",
"ecr:GetDownloadUrlForLayer",
"ecr:GetRepositoryPolicy",
"ecr:DescribeRepositories",
"ecr:ListImages",
"ecr:DescribeImages",
"ecr:BatchGetImage",
"ecr:GetLifecyclePolicy",
"ecr:GetLifecyclePolicyPreview",
"ecr:ListTagsForResource",
"ecr:DescribeImageScanFindings"
],
"Resource": "*"
}
]
}
- Host:
docker.io - Username:
[your username] - Password:
[your password]
For legacy GCR
- Host:
gcr.io - Username:
_json_key - Password:
[full GCP service account JSON]
The service account must have the following IAM roles on the artifacts.your-gcp-project.appspot.com Google Cloud Storage bucket:
resourcemanager.projects.get
resourcemanager.projects.list
storage.objects.get
storage.objects.list
storage.buckets.get
storage.buckets.list
For pkg.dev
- Host:
{region}.pkg.dev - Username:
_json_key - Password:
[full GCP service account JSON]
The service account must have the following IAM roles on the artifact registry
roles/artifactregistry.reader
roles/artifactregistry.writer
roles/artifactregistry.createOnPushWriter
- Host:
quay.io - Username:
[your username] - Password:
[your password]
- Host:
ghcr.io - Username:
[your GitHub username] - Password:
[your GitHub token]
- Host:
[your domain].jfrog.io - Username:
[your username] - Password:
[your JFrog identity token]